Introduction
Much of my work over the last decade has centered around modernizing aging equipment in manufacturing environments. These are not flashy projects. They rarely get the spotlight. But the reality is that they are absolutely essential to the long-term health and performance of a facility. Modernization is not always a popular conversation. Most leaders prefer to focus on growth, production targets, or new equipment that enables expansion. Very few are excited about spending capital to upgrade something that is still running. That hesitation is understandable. I have heard it from plant managers, maintenance supervisors, and operations executives in nearly every facility I have worked in. The equipment is working. The line is running. The KPIs are green. Why touch anything?
That is a reasonable perspective on the surface. But the truth is that modernization is not about replacing things that are broken. It is about recognizing when continued reliance on aging systems introduces risks that are no longer acceptable. Equipment might appear to be working, but behind the scenes, you may be dealing with unsupported hardware, software running on legacy operating systems, components that are no longer available from the OEM, or systems that only a single technician knows how to operate. These are not hypothetical risks. They are real situations I have encountered repeatedly in the field. Left unaddressed, they create operational fragility. Eventually, something gives. When it does, it is no longer a technical discussion. It becomes a business problem.
To give you a bit of context on how I approach these topics, I began my career at one of Procter and Gamble’s most advanced manufacturing sites, where I led automation and control system projects that supported both production operations and R&D. That role gave me exposure to highly integrated systems and set the foundation for understanding how world-class operations function. I later joined Kraft Heinz in a maintenance leadership position where I was directly responsible for equipment reliability, technician performance, and process improvement. It was a very different environment, but one that taught me how to deliver results with the resources on hand and how to prioritize what truly matters when capital is limited. Following the closure of that facility, I moved into a consulting and integration role where I led control system upgrades, SCADA deployments, MES rollouts, and data infrastructure projects for clients like Kraft Heinz and Post Holdings. Along the way, I completed an MBA at McGill University and co-founded a startup on the IT side, which deepened my understanding of cloud infrastructure and digital systems at scale. Today, through Joltek, I work with manufacturing teams of all sizes to help them assess their current systems, identify modernization needs, and implement upgrades that align with both operational and strategic goals.
This article is a direct reflection of that experience. My goal is not to present a generic case for modernization. You do not need another high-level explanation of Industry 4.0 or a vendor pitch full of buzzwords. Instead, I want to walk you through the real-world complexities of modernization from the inside. I will share what I have seen work, where companies get stuck, and how to make smart decisions even when the path forward is not obvious. We will look at why modernization is necessary even when equipment is functioning, how to evaluate the current state of your systems, how to manage OEM hardware obsolescence, what cybersecurity risks should be on your radar, and how to build a roadmap that balances risk, cost, and uptime. I will also outline how organizational maturity affects these efforts and what to expect when engaging with teams at different stages of readiness.
Whether you are a plant manager trying to prevent unexpected failures, an engineering leader navigating legacy systems, or a director of operations looking to ensure resilience across your sites, this article is written for you. Modernization does not need to be disruptive. It can be planned, phased, and executed with minimal impact on production. But it requires the right framework, the right insight, and a clear understanding of both the risks and the opportunities. That is what I want to offer here.
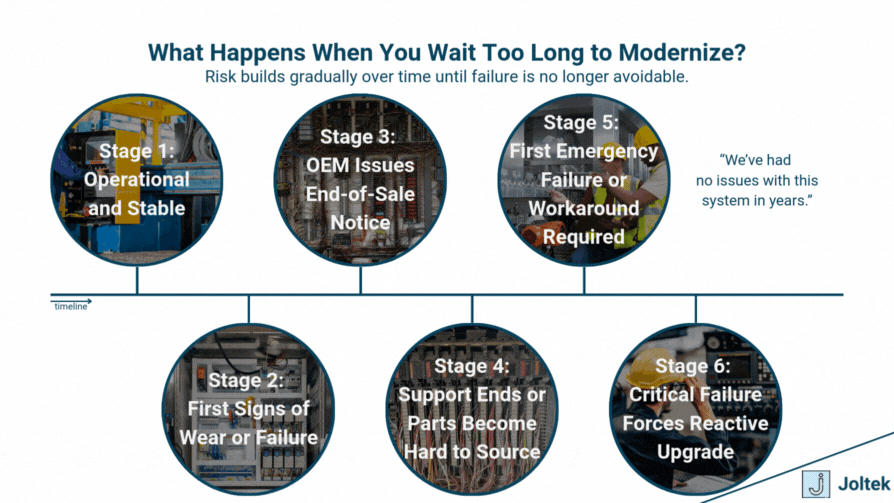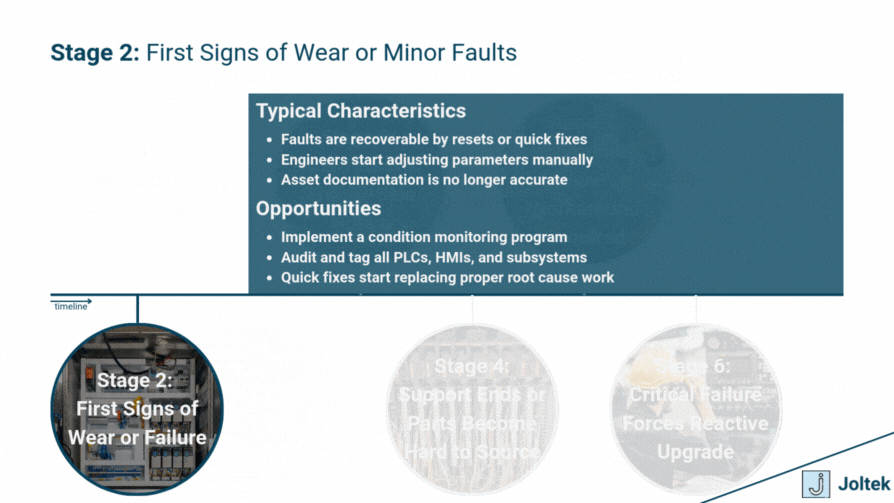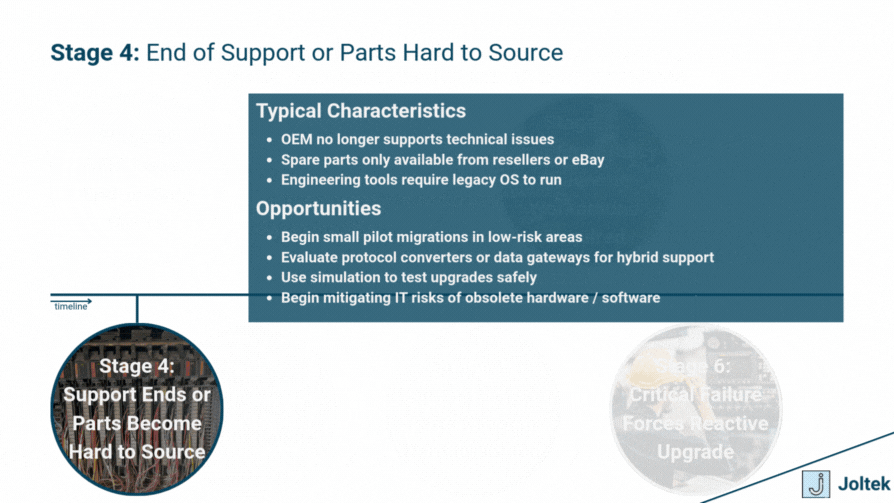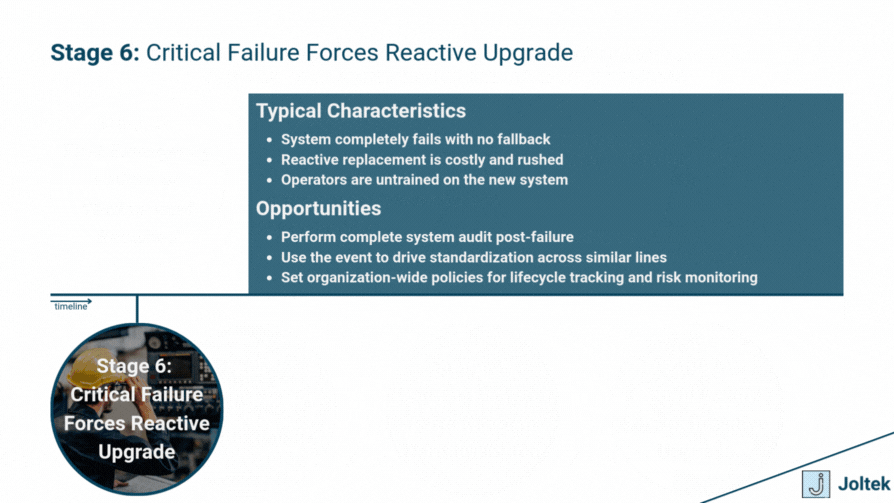
Why Modernize Obsolete Equipment
In nearly every facility I have worked in, there is one line I hear more than any other when modernization is brought up. If it is running, do not touch it. This mindset is deeply ingrained in many manufacturing environments, and I understand why. Production is the heartbeat of a plant, and no one wants to risk interrupting it. If a piece of equipment is still functional and output is meeting expectations, any conversation around upgrading it can easily be seen as unnecessary or premature. But over time, I have learned that this perception hides a growing problem. What is running today may be quietly becoming a liability. By the time the symptoms show up, the options are fewer, the costs are higher, and the urgency is unavoidable.
The true cost of inaction is rarely visible in a single downtime event. It is cumulative. It shows up in unplanned maintenance hours, increasing response times, parts that take weeks to source, or systems that only one person on the team knows how to troubleshoot. In some cases, it is a control panel running on an operating system that has not been supported for over a decade. In others, it is a piece of critical software that was written by someone who left the company years ago, with no documentation in sight. These situations do not seem urgent until something breaks, or until a new requirement pushes your existing systems beyond what they can handle. And by then, the decision is no longer about strategy. It becomes a matter of crisis response.
Common Triggers for Modernization
Modernization rarely happens because someone wakes up one day and decides to replace a working system. It typically begins with a trigger. One of the most common is a hardware failure that exposes the fragility of the system. Maybe a legacy PLC goes down and there are no spares in stock. Maybe a VFD controller fails and the only replacement available is on eBay. These moments are painful and often expensive, but they also serve as a wake-up call. Another common trigger is sourcing challenges. When OEMs sunset their product lines, spare parts begin to disappear. Even if the component is still functional, your team might be relying on a shrinking pool of inventory that can no longer be replenished through official channels. This becomes even more difficult when global supply chains are stretched, or when corporate procurement policies restrict purchasing from third-party sources.
In other cases, compliance requirements or customer mandates force a reassessment of aging systems. If a plant undergoes an audit and it becomes clear that certain equipment no longer meets safety, quality, or documentation standards, the conversation changes quickly. The same applies when corporate initiatives around digital transformation highlight systems that cannot generate usable data or cannot integrate with MES or ERP platforms. In these cases, it is not about the equipment breaking. It is about the equipment not being compatible with the direction the business is trying to go. This is especially true when leadership begins asking for real-time visibility or when there is a push to consolidate systems across multiple sites.
Understanding Equipment Criticality and Process Dependency
Not all equipment is created equal. One of the most important concepts in planning a modernization strategy is understanding equipment criticality. If a piece of hardware is supporting a low-volume, low-risk process, then delaying an upgrade may be justifiable. But if that same piece of hardware is part of a bottleneck operation, or if it supports a safety-critical function, then the stakes are much higher. The more a process depends on a single point of failure, the more urgent it becomes to evaluate its long-term viability. I have seen situations where a single controller failure stopped an entire line for multiple days. In those cases, the cost of inaction far outweighed the cost of a planned upgrade.
Dependency also matters when considering support resources. If only one or two technicians know how to maintain a particular system, or if the programming environment is outdated and incompatible with current engineering tools, then every day you delay modernization increases operational risk. These risks are not always visible to leadership, which is why clear communication between engineering, maintenance, and management is essential.
The Role of Policies, Customers, and External Pressures
Modernization is not always driven internally. In some facilities, corporate policies or customer requirements play a significant role. For example, a food or pharmaceutical manufacturer may need to meet specific regulatory standards that are not possible with aging systems. I have also seen customer audits uncover control systems that were non-compliant with updated traceability or reporting requirements, forcing the plant to upgrade ahead of schedule. In these cases, modernization becomes non-negotiable.
There is also the growing pressure from insurance providers and cybersecurity audits. If a facility is still relying on unsupported operating systems or exposed networks, it is only a matter of time before someone from IT or risk management raises concerns. These concerns are often linked to cost implications on premiums, or in some cases, eligibility for certain types of coverage. These are conversations that start in the boardroom but quickly make their way to the plant floor.
Safety, Environmental, and Long-Term Sustainability Risks
Modernizing obsolete equipment is not just a technical decision. It is also about protecting people and the environment. As systems age, the likelihood of failure increases, and that failure can sometimes result in more than just downtime. I have seen safety interlocks fail due to outdated logic controllers. I have seen environmental monitoring systems that were no longer accurate because the sensors and data collection tools were no longer reliable. In regulated industries, these gaps can result in fines, shutdowns, or worse. Even in less regulated spaces, there is a growing expectation that facilities operate responsibly and transparently. Relying on obsolete control systems makes it difficult to meet those expectations.
The goal of modernization is not to chase the latest technology for its own sake. It is to ensure that your systems are resilient, your teams are supported, and your plant can continue to operate effectively in a changing environment. That requires a clear understanding of what is at risk, what is working, and what is quietly becoming a liability. In the next section, we will look at how to recognize obsolescence in your systems and what to do about it before it becomes a crisis.
Understanding Your Installed Base
One of the most overlooked steps in any modernization project is understanding what systems are actually in place. It is surprisingly common for facilities to run critical operations without having a clear or current inventory of their control systems. While most plants have some form of asset tracking in place, what is typically missing is a detailed view of the automation and data infrastructure that supports production. Without this foundational knowledge, it becomes nearly impossible to plan effectively, evaluate risk, or execute upgrades with confidence. Modernization starts with visibility and visibility begins with an accurate installed base assessment.
Most organizations can quickly point to a list of physical equipment such as packaging lines, mixers, or conveyors. But that is not enough. You also need a complete and accurate record of the control systems that run that equipment. This includes every programmable logic controller, human-machine interface, SCADA node, historian server, and every piece of network infrastructure that connects them. It also includes subsystems like variable frequency drives, servo motors, barcode scanners, vision systems, industrial PCs, and sensors. These components are often embedded within machines or mounted inside panels and may not be tracked in traditional asset management systems.
What Should Be Captured
A proper installed base inventory goes far beyond just model numbers. You need to capture the make, model, firmware version, and physical location of every critical control system component. For each programmable controller, you should know whether it is currently supported by the OEM, whether it is included in any active service contracts, and whether backups of the logic programs exist. The same goes for HMIs and SCADA servers, where it is important to document software versions, operating systems, and licensing status. I have walked into many plants where the only person who understood how a legacy system worked had already retired, and the last known backup was stored on a USB stick no one could find. These are the kinds of situations that can turn a minor failure into a major crisis.
Networked components deserve special attention as well. Industrial switches, routers, and protocol converters are often tucked away in cabinets and forgotten until they fail. These are vital parts of your infrastructure and should be documented like any other piece of equipment. Even more important are the subsystems that quietly support key functions. Drives, vision systems, weight checkers, and other specialized devices can quickly become the source of delays if they are not properly tracked.

How to Build and Maintain an Installed Base Inventory
There are several methods to build an accurate picture of your control systems. The most reliable but also the most time-consuming is a manual audit. This involves walking the floor, opening panels, checking nameplates, and cross-referencing what is in the field with what is stored digitally. While it requires time and coordination, it is often the only way to truly uncover what exists, especially in facilities that have undergone years of incremental upgrades or emergency repairs.
For more advanced operations, network scanning tools can accelerate the process. These tools can automatically detect IP-addressed devices on the control network and identify their make, model, and firmware versions. While this does not cover everything, especially devices that are hardwired or offline, it provides a strong baseline that can be verified and expanded through manual checks. However, using these tools effectively requires coordination with both IT and OT teams, particularly in environments with strict security protocols or segmented networks.
Another option is to leverage computerized maintenance management systems or enterprise asset management platforms, provided they are configured to include automation components. In some facilities, these systems are already used to track spare parts, work orders, and preventative maintenance schedules. Adding structured fields for control systems can help centralize information, although it often requires a deliberate effort to make this data complete and usable.
Why Poor Documentation Creates Long-Term Risk
A lack of documentation is more than just an inconvenience. It creates technical debt, which refers to the hidden cost of systems that become harder to maintain, modify, or replace over time. Every time an undocumented change is made, or a new component is added without updating records, the complexity of your environment increases. Over months and years, this leads to brittle systems that no one fully understands. When something goes wrong, recovery takes longer, costs more, and introduces more risk. The longer you wait to create a full system inventory, the more exposed your operation becomes.
I have seen entire teams scramble to recover from an unplanned shutdown, only to realize that no one knew how to reload the program into a failed controller. I have also seen companies pay for rush replacement parts, only to discover that the failed component had been obsolete for years and could no longer be sourced. In both cases, the core issue was not the failure itself. It was the lack of structured, current information about the installed base.
Tools and Templates That Help
One practical way to improve documentation is through data mapping templates that allow you to track each component along with its location, status, and lifecycle stage. For example, a good template will include fields for asset ID, manufacturer, part number, firmware version, software version, network address, last backup date, and whether the component is considered active, phased out, or obsolete. By tagging equipment based on lifecycle status, you can begin to prioritize upgrades and forecast replacement needs in a structured way. This allows engineering and maintenance teams to speak with clarity when presenting upgrade proposals to leadership.
Ultimately, the purpose of documenting your installed base is to reduce guesswork and increase confidence. It gives your team a solid foundation to make informed decisions, whether you are troubleshooting an issue, planning a migration, or preparing for an audit. Without this foundation, modernization becomes reactive, expensive, and unpredictable. With it, you gain the ability to act strategically and avoid surprises.
OEM Hardware Obsolescence
One of the most common triggers for modernization comes from the outside. When an OEM announces that a component is being phased out, that announcement marks the beginning of a timeline that often goes unnoticed until it is too late. Understanding how OEM hardware lifecycles work and how to respond appropriately is one of the most important skills for anyone responsible for keeping automation systems running. Whether you are managing a single line or a network of facilities, ignoring these lifecycle milestones introduces real operational risk.
Understanding the OEM Lifecycle
Every major OEM including Rockwell Automation, Siemens, Schneider Electric, Phoenix Contact, Festo, and others follows a structured product lifecycle. This typically includes a sequence of stages such as active sale, active support, limited support, and finally complete retirement. While terminology may vary, the most important milestones to track are End of Sale, End of Support, and End of Life. End of Sale means that you can no longer purchase the product through official channels. End of Support means that firmware updates, spare parts, and engineering assistance are no longer guaranteed. End of Life is the final stage, where the OEM formally retires the product and ceases all forms of service.
In my experience, many manufacturers underestimate how quickly these transitions happen. OEMs typically communicate these changes through technical bulletins, lifecycle notices, and migration guides. These are usually posted on the company’s website or distributed through sales channels. The problem is that these documents rarely make their way to the plant floor or the engineering team unless someone is actively monitoring them. If you are not subscribed to lifecycle alerts or do not have a vendor relationship that keeps you informed, it is easy to fall behind.
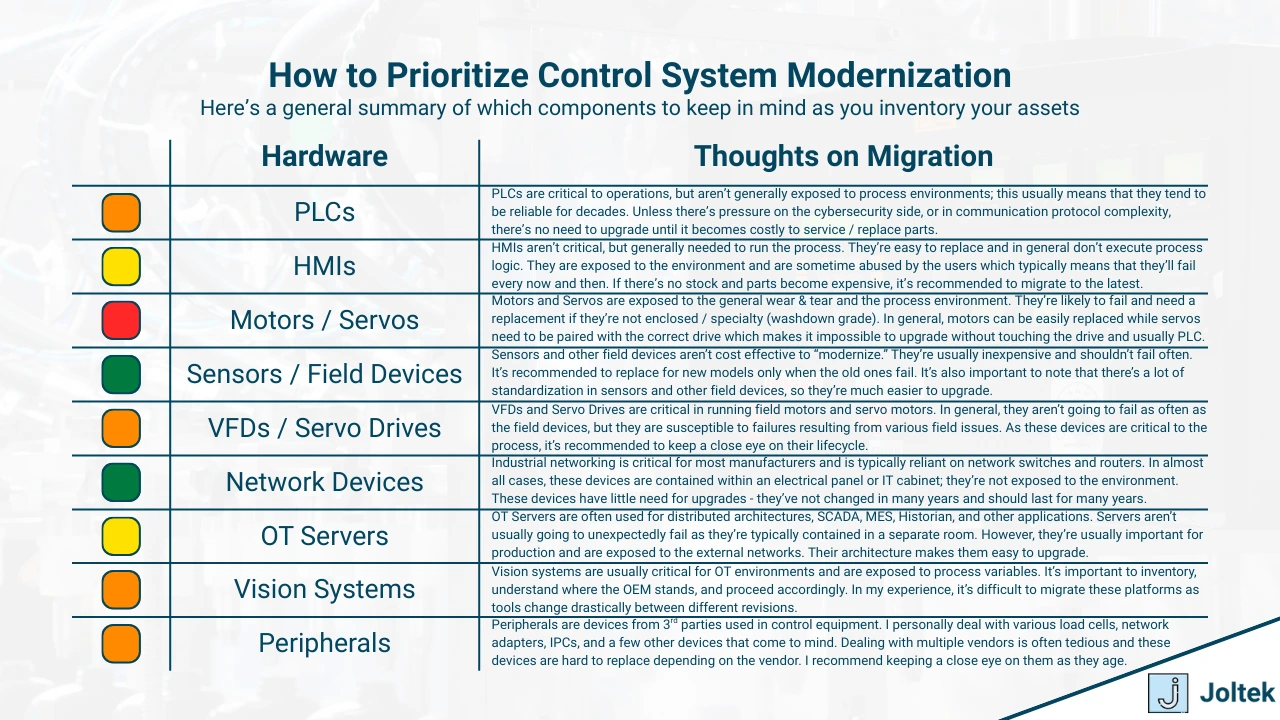
Nature of Equipment and Risk Prioritization
Not all equipment should be treated the same. One of the first things I teach clients when we begin a modernization review is that you must prioritize based on both failure risk and operational impact. Some components are mission-critical. Others can fail without significant consequence. The key is understanding how each piece of hardware fits into your process and how likely it is to cause disruption if it stops working.
Certain types of equipment are inherently more durable than others. A properly installed PLC can run for decades with no issues. An HMI touchscreen may wear out after only a few years. A VFD or servo controller might sit in a cabinet untouched for months but fail when ambient conditions change or when stress events occur. These differences matter when planning your approach to obsolescence. They also affect how you interpret failure curves. Many industrial components follow what is commonly referred to as the bathtub curve. This curve reflects three phases of failure risk. The initial period of early-life failures, a long stretch of stable performance, and a final wear-out phase where risk increases sharply. If your components are entering this last stage and are no longer supported, the cost of waiting grows with each passing quarter.
The Real Cost of Migration
Upgrading obsolete equipment is rarely as simple as removing one component and installing another. In fact, the cost of migration can often exceed the price of the hardware itself. There are engineering hours required to redesign control panels, validate software compatibility, reprogram PLC logic, and ensure that all safety and production functions still work as intended. Operator interfaces may need to be rebuilt. Communication protocols may need to be adapted. Panel layouts might need to be adjusted for new form factors. Even small changes can introduce ripple effects that take time and effort to resolve.
Another factor that is often overlooked is downtime planning. When you touch live systems, especially in production-critical areas, you must schedule installation and commissioning carefully. In some cases, this can be done during planned outages. In others, it requires off-shift work or special coordination with operations. I have seen migrations that took only two hours of install time but required two weeks of planning to avoid disruption. This is especially true when the upgrade involves validation protocols or regulated environments where software and hardware changes must be documented, tested, and approved.
Finally, it is important to consider operator and technician training. A new control system may offer better features, but if your team does not understand how to use or maintain it, the benefits will be limited. Part of any effective migration plan should include documentation updates, training sessions, and a clear knowledge transfer process to support long-term ownership by your internal team.
Spare Parts and Lifecycle Management
Spare part strategy is one of the most powerful but underutilized levers in extending the life of legacy equipment. When a product is no longer sold by the OEM, your only options are to source from existing inventory, purchase through third-party vendors, or salvage from other equipment. Knowing how long your current stock will last is a fundamental piece of the risk assessment. If you have three spare units of a legacy controller and they fail once per year, you might be covered for three years. But if failure rates increase, or if a supplier unexpectedly dries up, that timeline shortens fast.
Some organizations rely on internal stocking strategies, where critical components are purchased in bulk ahead of obsolescence and stored in climate-controlled environments. Others look at cannibalization, where equipment from retired or underutilized lines is harvested for parts. I have also seen facilities build strategic relationships with third-party vendors who specialize in second-hand or refurbished components. These sources are not ideal for the long term, but they can be valuable in bridging the gap between failure and full migration.
To make smart decisions in this area, you need to model spare part consumption based on historical failure rates, current usage patterns, and supplier availability. This allows you to forecast the point at which continued operation becomes risky and helps you make the case for proactive investment. Without this analysis, decisions are often made reactively, which usually leads to higher costs and more stress on your team.
Ultimately, managing OEM obsolescence is about timing. Move too early and you waste capital on unnecessary upgrades. Move too late and you pay for emergency response, lost production, and system instability. The goal is to act with enough foresight to control the outcome rather than be controlled by the circumstances. In the next section, we will look at the cybersecurity risks that arise when legacy systems remain in place and how those risks affect both operational reliability and compliance expectations.
Cybersecurity Risks of Obsolete Equipment
Cybersecurity is a topic that still feels abstract for many manufacturing leaders, especially those who have spent most of their careers focused on physical systems, process controls, and production targets. But in recent years, it has become clear that cybersecurity is no longer just an IT concern. It is a direct threat to operational continuity. For facilities running legacy equipment, that threat is even more pressing. The unfortunate reality is that older control systems were not designed with security in mind. They were designed for reliability, speed, and simplicity. In an era where those systems were isolated from the outside world, that approach made sense. Today, however, connectivity is everywhere. And with connectivity comes exposure.
Most legacy systems lack even the most basic security controls. I have worked in facilities where production-critical equipment was still running on Windows XP or Windows 7, often with no patching strategy and no real access restrictions in place. These systems are often directly connected to the plant network and in some cases accessible through remote desktop software or vendor-installed backdoors. Even when teams believe that they are protected by air gaps, I have seen situations where USB drives, engineering laptops, or unsecured wireless bridges introduced risk without anyone realizing it. The assumption that physical isolation is sufficient no longer holds up in modern industrial environments.
Vulnerabilities in Legacy Platforms
Older PLCs, HMIs, and SCADA software often include well-documented vulnerabilities that have been publicly disclosed through national and international security databases. These vulnerabilities are not theoretical. They are specific issues that have been identified, published, and in many cases actively exploited in the field. The Common Vulnerabilities and Exposures database, often referred to as CVE, is a public resource that tracks known weaknesses in software and firmware. Many legacy control systems appear in this database, often with critical severity scores.
In addition to known vulnerabilities, many older systems do not support modern security features such as authentication, encryption, or access control. This means that anyone who gains access to the network can potentially access, modify, or disable control logic without detection. In some environments, I have seen entire production lines that can be reprogrammed using a generic engineering workstation with no password required. That level of exposure is difficult to justify, especially in industries that are subject to regulatory oversight or where customer expectations around traceability and security are increasing.
Growing Attention from Insurers and Regulators
What makes cybersecurity even more relevant today is the growing attention it is receiving from insurers and regulatory bodies. In the past, a cyberattack on a manufacturing facility might have been considered an outlier or an IT issue. That is no longer the case. Insurance providers are now closely evaluating the technical posture of manufacturing clients, particularly when it comes to outdated operating systems, unsupported software, and unsecured remote access solutions. In some cases, these evaluations are already affecting premiums. In others, they are driving changes in underwriting criteria that may result in limited coverage for facilities that are seen as high risk.
Regulators are also beginning to address the intersection of cybersecurity and industrial systems. In Europe, new laws are being introduced that create financial penalties for companies that fail to protect critical infrastructure. These regulations are expected to influence North American standards over time. Whether or not your facility is currently subject to these rules, the direction is clear. Cybersecurity is becoming a cost of doing business, and the cost of noncompliance is rising.
Frameworks and Tools That Help
For manufacturers who want to take a more structured approach, there are several frameworks that can help guide the process. The ISA IEC 62443 standard is designed specifically for industrial automation and control systems. It provides a layered approach to security that includes asset identification, network segmentation, access control, and ongoing monitoring. Similarly, NIST 800 82 offers guidance for securing industrial control systems within a broader cybersecurity strategy. These frameworks are not quick fixes, but they provide a strong foundation for building a resilient system over time.
At a practical level, the use of vendor advisories and vulnerability databases can help your engineering and IT teams stay ahead of known threats. Most major OEMs now publish regular security bulletins that include recommendations for patching, configuration changes, or product replacements. These bulletins are often overlooked by plant teams who are focused on daily operations, but they are a vital source of insight into where your risks might be growing. Even without making immediate changes, simply knowing what vulnerabilities exist within your system is the first step toward managing them.
Making the Case Internally
One of the challenges I often see is that cybersecurity risks are hard to quantify in traditional manufacturing terms. You can calculate the cost of a failed motor or the value of a production line going down, but it is harder to assign a dollar figure to a potential cyber event that has not yet happened. That is why it is important to frame the conversation in terms of risk exposure, operational resilience, and business continuity. A cyber incident that affects a critical control system can stop production, delay shipments, damage customer relationships, and erode trust in your technical leadership. In some industries, it can even affect safety and compliance.
Modernizing control systems is not only about functionality or uptime. It is also about security. If your equipment is no longer supported, if your software cannot be patched, or if your systems lack basic access control, then every day that passes increases your exposure. In the next section, we will explore how to evaluate your control systems through structured assessments and audits that help quantify risk, prioritize upgrades, and create a clear roadmap for modernization.
Framework for Control System Assessment and Audit
Before you can modernize with confidence, you need to understand exactly what you are working with. Many facilities attempt to plan upgrades based on assumptions, vendor pressure, or immediate pain points. But real modernization should be driven by a clear and structured understanding of your systems. That is where a control system assessment becomes essential. This is not just a list of equipment or a quick site walk. It is a comprehensive evaluation of your automation infrastructure, designed to help you quantify risk, uncover blind spots, and make informed decisions about what to upgrade, when, and why. A strong assessment provides both the technical clarity and the business justification needed to drive modernization forward.
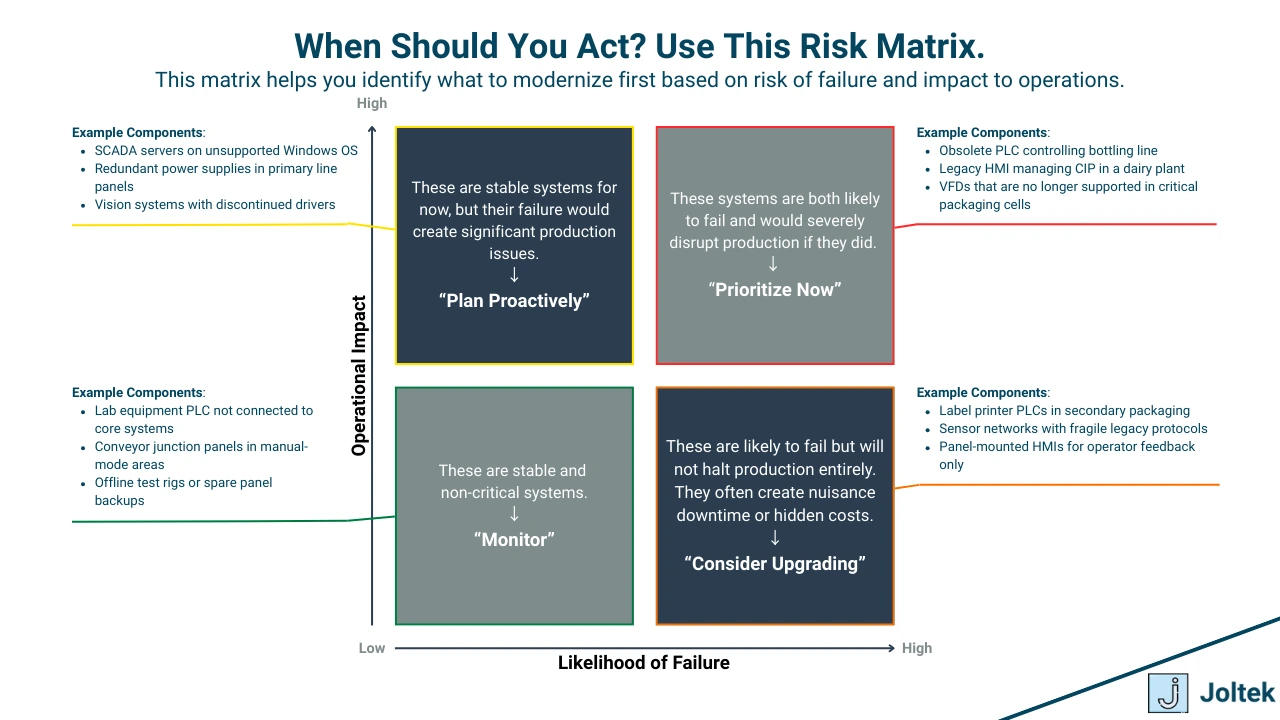
Core Components of an Assessment
The first step in any assessment is a detailed hardware inventory. This goes beyond asset tags or maintenance logs. You need to know exactly which controllers, drives, HMIs, industrial PCs, and peripheral devices are installed across the plant. Each component should be documented with its model number, firmware version, manufacturer, physical location, and lifecycle status. It is equally important to identify which parts are obsolete, which are nearing obsolescence, and which are still fully supported. Without this information, it is impossible to prioritize your efforts or evaluate where you are most exposed.
Next is the software inventory. Many manufacturers overlook this piece, assuming that if the hardware works, the software is not a concern. But that could not be further from the truth. Unsupported operating systems, unlicensed applications, outdated SCADA platforms, and forgotten configuration tools all contribute to risk. During the assessment, every major application should be catalogued with its current version, licensing status, patch level, and support standing. You should also identify any software that is tied to individual engineering laptops or external vendors, as this often creates hidden dependencies.
Equally important is a review of the network topology. This means mapping out how all devices are connected, what protocols are in use, where traffic flows, and which systems are exposed to external interfaces. Network segmentation, firewall rules, and access control policies should be reviewed carefully. In many plants, the network has evolved over time with minimal documentation. What starts as a clean architecture quickly becomes tangled through years of line upgrades, emergency installs, and vendor shortcuts. Understanding the current state of your control network is essential for both modernization and cybersecurity planning.
Another key element is the failure and support profile of each system. The assessment should capture known issues, failure frequency, mean time to repair, and availability of support resources. If only one person knows how to service a certain controller, or if a particular drive has failed multiple times in the past year, that information needs to be captured and factored into your risk model. This is also where you can begin to apply structured risk scoring and prioritization. Every asset can be evaluated based on factors such as criticality, failure history, obsolescence level, and replacement complexity. By scoring assets using these criteria, you begin to build a heat map that shows where attention is most urgently needed.
What the Assessment Should Deliver
A well-run control system assessment should always deliver a clear set of outputs. The first is a red yellow green asset map, which categorizes each system by its level of risk. Red assets are high priority and often include obsolete hardware or unsupported systems with high operational impact. Yellow assets are still functional but carry known risks that need to be monitored or addressed in the near term. Green assets are healthy and require no immediate action. This simple framework gives executives and operational leaders an immediate view of where the facility stands.
The second key deliverable is a migration roadmap. This outlines which systems should be upgraded first, what technologies can be standardized across the plant, and how modernization should be phased to avoid disruption. The roadmap should be tied to real timelines, including preparation, installation, commissioning, and training. Ideally, it also includes resource planning and identifies whether internal staff or external partners will be required to execute the work.
The third deliverable is a budget and resource estimate. This includes capital costs for hardware and software, engineering time for design and implementation, and operational costs such as downtime planning and training. Many facilities fail to move forward with modernization because the investment feels overwhelming or unclear. Providing a detailed but flexible estimate helps make the case for staged investment and shows leadership that there is a real plan in place.
How to Conduct a Thorough and Credible Assessment
The process itself matters just as much as the output. A strong assessment combines technical evaluation, stakeholder engagement, and on-site observation. That means walking the floor, opening panels, interviewing operators and technicians, and observing how systems are actually being used. It is common to discover that certain systems are running in ways that differ from how they were designed, or that undocumented changes have been made over time. These insights are only possible when you engage the people who work with the equipment every day.
It is often beneficial to involve a third-party consultant or systems integrator during the assessment. Internal teams bring valuable context, but external support can provide objectivity, industry benchmarks, and specialized tools that make the process more effective. An outside perspective can also help facilitate difficult conversations around risk and investment without the internal politics that sometimes get in the way.
Finally, it is critical to present findings in a way that resonates with decision-makers. Executives do not need to see wiring diagrams or controller part numbers. They need to understand what is at risk, what it will cost to fix it, and how it ties back to business outcomes. That means framing the results in terms of risk exposure, operational continuity, compliance readiness, and long-term cost avoidance. When presented clearly, the results of an assessment can open the door to budget approvals, cross-functional alignment, and immediate next steps.
A control system assessment is not just an audit. It is the foundation for smart modernization. It gives you the data, the structure, and the confidence to act before failure forces your hand. In the next section, we will explore how to turn these findings into a practical migration strategy that respects production realities and builds toward a stronger, more resilient future.
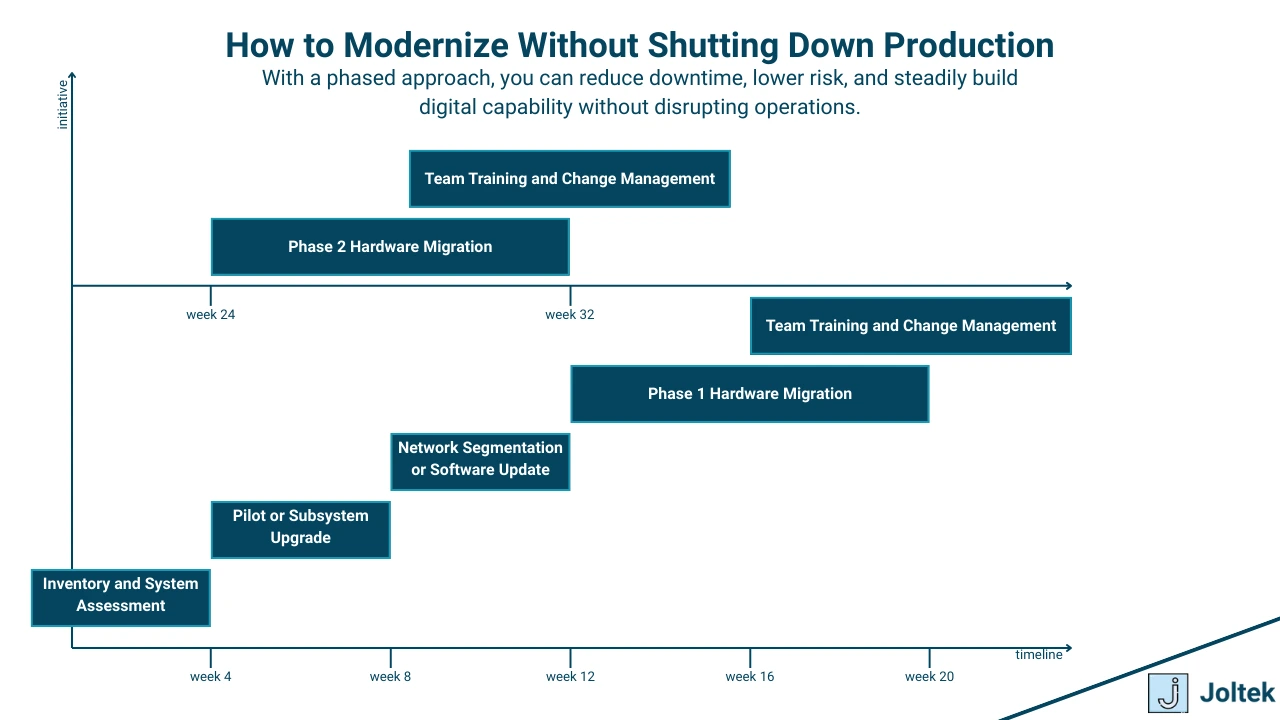
Strategies for Modernization Without Disruption
One of the biggest concerns I hear when talking to operations leaders about modernization is the fear of disruption. The idea of replacing or upgrading production-critical systems immediately raises questions. How long will the line be down? What if the new equipment does not work as expected? Do we have the people needed to support the change after it is installed? These are valid concerns. In many facilities, even a few hours of unplanned downtime can have ripple effects that impact production schedules, labor planning, and customer commitments. That is why a successful modernization strategy must be designed with minimal disruption in mind. Upgrades can and should be executed in a way that respects production, protects uptime, and builds internal confidence.
Planning Through Phased Implementation
The most effective modernization efforts are structured into phases. Rather than replacing entire systems all at once, you begin with clearly defined segments of work that can be completed independently. This might involve isolating a specific line, cell, or subsystem that can be upgraded without affecting the broader operation. In many of the projects I have led, we start by upgrading HMIs or data infrastructure while leaving the core control hardware untouched. This allows us to introduce new capability and build familiarity with the new tools before performing deeper changes.
A phased approach also makes it easier to align with planned downtime windows. Many manufacturers have periodic maintenance shutdowns or slow production periods that can be leveraged for installation and commissioning. When you already have a list of pre-scoped modernization tasks ready to go, you can make better use of those windows and avoid last-minute coordination. The key is to plan proactively and treat modernization like a rolling program rather than a one-time event.
Shadow Mode and Parallel Testing
One of the most powerful tools for modernization without disruption is the use of shadow mode or parallel testing. This means running the new system side by side with the legacy system, without yet handing over control. For example, you can connect a new SCADA or MES system to your PLCs in a read-only capacity and begin collecting data before using it for any operational decisions. You can also develop and test PLC programs in a simulated environment or on a test bench that mirrors production conditions.
Shadow mode allows you to validate that the system performs as expected without introducing risk. It also provides a way to train staff and refine configuration before full deployment. In several of the projects I have delivered, this technique has allowed us to go live with confidence, knowing that the software had already been tested with real data and the team was comfortable with the interface.
Pilot Projects and Low-Risk Systems
A common mistake I see is trying to modernize the most critical parts of the facility first. While it might seem logical to address the biggest risks immediately, it often makes more sense to begin with pilot lines or non-critical systems. These environments offer a lower-risk testing ground where new technologies, standards, and processes can be introduced. You learn what works, where the gaps are, and how your team responds to change.
Once a pilot has been completed successfully, it becomes much easier to scale the approach to higher-value assets. You can show proof of concept, quantify the benefits, and reduce resistance from stakeholders who may be skeptical. Pilots are also a valuable way to establish internal champions who can support future phases of the project.
Bridging New and Legacy Systems
Modernization rarely involves a clean break from the past. In most cases, new systems must coexist with older ones, at least for a period of time. That is why it is critical to plan for integration between legacy and modern platforms. This often involves the use of protocol converters, data gateways, and edge devices that allow old hardware to communicate with new applications. I have used these tools extensively to bring legacy PLCs online with MQTT brokers, cloud dashboards, and modern SCADA systems.
The goal is not to force a complete change overnight. It is to gradually build interoperability so that modernization can proceed at a sustainable pace. By integrating new systems incrementally, you allow operations and maintenance teams to adapt without overwhelming them. You also reduce the pressure to upgrade everything at once, which is rarely practical from a cost or resourcing perspective.
Training and Team Readiness
Technical success means nothing if the people on the floor are not prepared to support the new system. That is why operator and maintenance training must be part of every modernization effort. This training should not happen after the installation is complete. It needs to be built into the rollout plan from the very beginning. The more involved your team is during commissioning and testing, the faster they will adopt the new tools and the more confident they will be when problems arise.
Training should be hands-on, role-specific, and supported by updated documentation. Your technicians need to understand how to troubleshoot the new hardware. Your operators need to know what to expect from the interface. Your engineers need to know where to find backups and how to modify programs safely. Empowering your team is one of the best ways to ensure that modernization delivers lasting value.
Supporting Change Management and Communication
Modernization is not just a technical shift. It is also a human one. Teams need to understand why changes are being made, how they will be supported, and what the impact will be on their day-to-day responsibilities. That is why clear communication and active change management are essential to the process. This includes regular updates to stakeholders, realistic timelines, and early identification of concerns that might slow things down.
In several of the projects I have led, I have seen how clear communication can be the difference between resistance and buy-in. When people understand the rationale behind a modernization effort and see that their feedback is being considered, they are much more likely to support the change. You do not need a formal change management department to do this well. You need transparency, alignment, and a commitment to listening.
Measuring Success
To build momentum and secure continued investment, you need to be able to measure the success of your modernization efforts. This includes hard metrics like reduced downtime, improved data accuracy, and faster changeovers. It also includes softer indicators like team confidence, fewer troubleshooting calls, and increased engagement from frontline staff. Over time, these outcomes build trust and create the foundation for future phases of modernization.
When you track performance, share results, and celebrate progress, you shift the mindset from hesitation to confidence. Modernization is no longer a threat to production. It becomes a tool to make production stronger, more resilient, and more efficient. In the final section, we will look at how to take everything we have discussed and use it to develop a long-term strategy that aligns technical improvements with business goals.
Conclusion
If there is one thing I have learned from working across dozens of manufacturing sites, it is that the risks of doing nothing far outweigh the discomfort of change. Legacy equipment does not announce when it will fail. Technical debt does not show up on a balance sheet until it becomes a problem. Unsupported systems, fragile networks, and undocumented control logic will continue to operate quietly until the moment they do not. And when that moment comes, the cost is often greater than what would have been required to act proactively.
Modernization is not just about upgrading technology. It is about preparing your operation for what comes next. Having a clear understanding of your installed base, the condition of your equipment, and the vulnerabilities in your infrastructure gives you a competitive advantage. It puts you in a position of control. With the right preparation, modernization can be a strategic process rather than a reactive one. This starts by getting the right inventory, mapping the risks, and building a plan that respects your operational priorities.
For many leaders, the idea of modernizing critical systems still feels overwhelming. It does not need to be. I have helped teams implement changes that were phased, deliberate, and non-disruptive to their core operations. I have seen how small wins, like cleaning up a network diagram or upgrading a single panel, can create momentum for larger changes. I have also seen the relief on a maintenance manager’s face when they know that the next failure will not bring the line down because a supported, well-documented system is already in place.
Modernization is not a one-time project. It is a manageable and strategic journey. Whether you are dealing with obsolete PLCs, aging SCADA systems, or a lack of data visibility, the most important step is simply to start. That might mean walking the floor to build an inventory. It might mean reviewing spare part stock with your maintenance team. Or it might mean reaching out to someone who can guide you through a structured audit.
If you are looking for support, this is exactly the kind of work we do at Joltek. We help manufacturers understand where they stand and where to go next. Whether you need a full control system assessment, help with planning a phased migration, or simply want to talk through your challenges, I invite you to reach out. You do not need to solve everything at once. But you do need to be intentional about where you are going. Modernization is possible. You just need the right approach and the right partner.










